We've been treated to some pretty entertaining feats of espionage courtesy of Hollywood. Who can forget the way Tom Cruise dangled from the ceiling as he attempted to crack into a computer security system in "Mission Impossible?" Or how about the mysterious hacker who seems to slip past every security to corrupt the Rossum Corporation's data in the "Dollhouse" television series? Hacking into a network must require superhuman skills and knowledge, right?
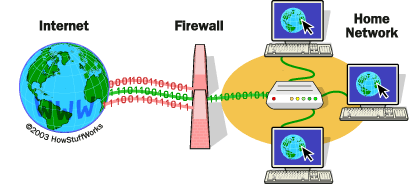
You might be surprised to learn how easy it is for someone to hack into a computer network. The fact is that many computer networks are practically defenseless to intruders. In the early days of home computer networks, the people who put the networks together were experts and enthusiasts. They put their systems together knowing how computers can communicate with each other and built in protective measures to prevent other computer users from snooping.
Advertisement
Today, home computer networks are popular among a broad range of consumers. User knowledge spans from expert to newbie. Some users may be unaware of the dangers they can encounter if they don't properly secure their network. Others may think home network security is too complicated or confusing. But network security is more important than ever and it's worth the effort to learn more about it.
An unprotected network could allow malicious hackers -- known as crackers -- access to your data. It might even allow someone to take control of your computers and use them to commit crimes like a distributed denial of service attack (DDoS). Even if no one snoops on your information or controls your computer, someone might use your network to access the Internet. As more ISPs begin to place caps on how much data you can download, it becomes even more important to control your network. You don't want to get slapped with a huge bill for Internet services you didn't even use.
With the right tools and knowledge, you can minimize your chances of having your security compromised by malicious hackers or computer viruses. Let's get started.
Advertisement